Why Cybersecurity Matters in Web Development
In today’s hyperconnected world, websites are no longer static brochures — they are dynamic platforms handling sensitive user data, financial transactions, and real-time interactions. As the complexity of web applications grows, so do the threats.
A single vulnerability can lead to data breaches, service downtime, loss of customer trust, and even legal consequences under regulations like GDPR and CCPA.
That’s why cybersecurity is not just an IT issue — it’s a core part of web development.
Common Web Security Threats Every Developer Should Know
Before we explore solutions, here are the most common attacks targeting web applications:
| Threat | Description |
| SQL Injection (SQLi) | Injecting malicious SQL queries to manipulate the database |
| Cross-Site Scripting (XSS) | Injecting scripts into web pages viewed by others |
| Cross-Site Request Forgery (CSRF) | Tricks users into performing actions without their consent |
| Remote File Inclusion (RFI) | Includes malicious files into a site via user inputs |
| DDoS Attacks | Overwhelming a site’s server with traffic to crash or slow it |
| Man-in-the-Middle (MITM) | Intercepting communication between user and server |
Cybersecurity Best Practices for Web Developers
Below are the essential tactics you should include in every web project — whether you’re building with WordPress, Node.js, React, or PHP.
1. Use HTTPS (SSL Certificate)
Always secure your site using HTTPS instead of HTTP. It encrypts communication between browser and server, protecting data from interception.
Tip: Most hosts provide free SSL certificates via Let’s Encrypt.
2. Sanitize User Inputs
Never trust user input — it could be malicious. Use validation and sanitization to prevent SQLi, XSS, and RFI.
Example in PHP:
$name = htmlspecialchars($_POST['name'], ENT_QUOTES, 'UTF-8');
In Node.js (Express + Validator):
const validator = require('validator');
const sanitizedInput = validator.escape(req.body.name);
3. Implement Content Security Policy (CSP)
CSP helps mitigate XSS by restricting where resources (scripts, styles, etc.) can be loaded from.
Example Header:
Content-Security-Policy: default-src 'self'; script-src 'self' https://trustedscripts.com;
4. Use Secure Authentication
- Enforce strong password policies
- Use OAuth2, JWT, or Two-Factor Authentication (2FA)
- Hash passwords using bcrypt, not MD5 or SHA1
Example with bcrypt (Node.js):
const bcrypt = require('bcrypt');
const hashedPassword = await bcrypt.hash(password, 12);
5. Limit File Uploads
If your app allows file uploads:
- Restrict file types (e.g., only .jpg, .pdf)
- Limit file size
- Store files outside the web root
- Scan files for malware
6. Keep Everything Updated
Outdated plugins, themes, libraries, and frameworks are major risk factors.
- Use tools like npm audit, Composer audit, or WPScan to identify vulnerabilities
- Enable automatic updates when possible
7. Install a Web Application Firewall (WAF)
WAFs filter, monitor, and block malicious traffic.
- For WordPress: Wordfence, Sucuri
- For general hosting: Cloudflare WAF, Astra
8. Use Environment Variables (Don’t Hardcode Secrets)
Store API keys, passwords, and other credentials in .env files or secret managers.
Example in Node.js:
const apiKey = process.env.MY_SECRET_API_KEY;
Never commit .env to version control!
9. Enable Logging and Monitor Activity
Track failed login attempts, user actions, and system errors.
- Use tools like Sentry, LogRocket, or Datadog
- Set up alerts for suspicious activities
10. Rate Limiting and Brute Force Protection
Prevent attackers from trying endless combinations.
In Node.js (Express):
const rateLimit = require('express-rate-limit');
app.use(rateLimit({ windowMs: 15 * 60 * 1000, max: 100 }));
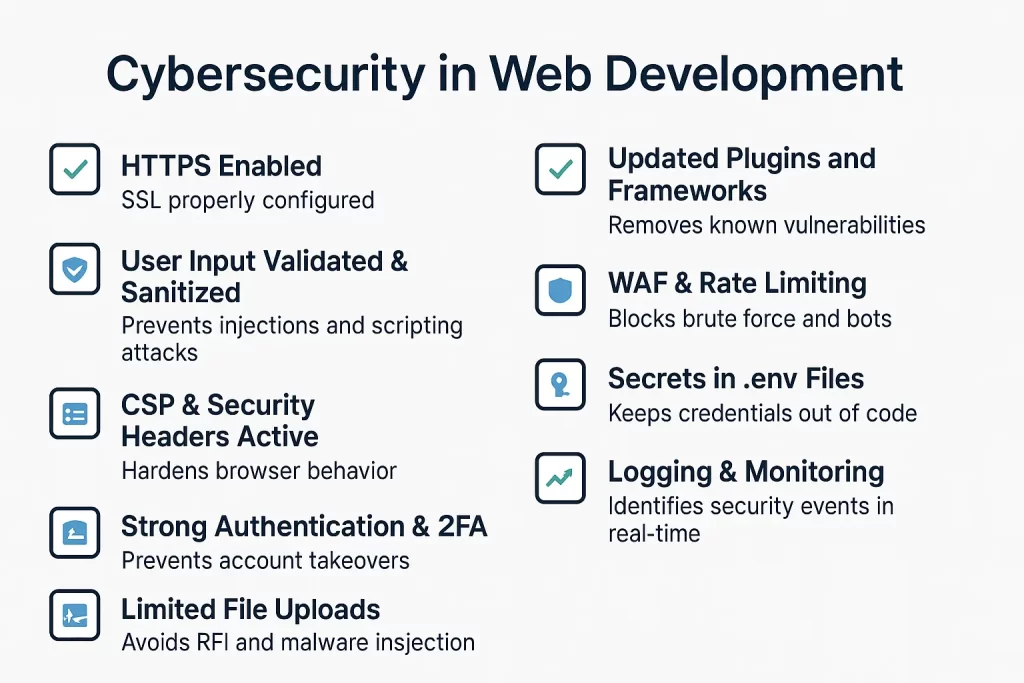
Cybersecurity Checklist for Developers
| Checklist Item | Description |
| HTTPS Enabled | SSL properly configured |
| User Input Validated & Sanitized | Prevents injections and scripting attacks |
| CSP & Security Headers Active | THardens browser behavior |
| Strong Authentication & 2FA | Prevents account takeovers |
| Limited File Uploads | OAvoids RFI and malware injection |
| Updated Plugins and Frameworks | Removes known vulnerabilities |
| WAF & Rate Limiting | Blocks brute force and bots |
| Secrets in .env Files | Keeps credentials out of code |
| Logging & Monitoring | Identifies security events in real-time |
Case Study: The Cost of Neglecting Web Security
In 2023, an unsecured contact form led to a data breach in a mid-sized eCommerce store. Attackers exploited an XSS vulnerability to steal session cookies, hijack user accounts, and siphon payment data.
The company faced:
- Loss of 4,500 customer records
- $30,000+ in chargebacks
- Reputational damage and negative media coverage
Moral of the story: A simple vulnerability can cause massive damage.
What the Future Holds
As AI tools and automation speed up development, attackers are also using AI to find vulnerabilities faster. That means developers must:
- Embrace DevSecOps
- Use code scanners and automated pentesting
- Stay educated with platforms like OWASP, HackerOne, or Bugcrowd
Final Thoughts
Cybersecurity isn’t a feature — it’s a foundation. Whether you’re building a static website or a SaaS platform, integrating secure development practices from day one is the best way to protect your users and your business.
Need secure web development support? Talk to Hatch2Web — we follow security-first practices across every stack: WordPress, Node.js, Laravel, React, and more.